Data Centre options for DDoS Mitigation
Fri, 8 Feb 2013
networking
Distributed Denial of Service attacks, or DDoS attacks, are a relatively common phenomenon for data centre clients. They are a means of denying a computer, usually a web server, the resources it needs to do its job of serving web pages and other data over the Internet. This denial can be done in a number of ways. The most common forms involve an attempt to saturate or overload either the bandwidth available to a server or the available web sessions a web-server can handle, thereby denying those resources to legitimate requests.
Victims of DDoS attacks are many and varied. Any high profile website is vulnerable
Political parties, government and military web-sites, banks and e-payment services are all vulnerable, as was proved by the well known Anonymous attack on Visa.com. Betting companies such as William Hill, Betdaq and Totalbethave become known victims of extortion from Mafia-like like groups who threaten to direct attacks at their websites during critical periods, such as major football matches or horse racing events.
Taking out well known websites is one of the ways we come to know about an attack. More often, however, attacks are visible through bandwidth flow analysis reports and alerts, such as those provided by Netflow Analyzer – see the video below for a quick understanding of how this works. ISPs will often see these sudden bursts on their network and in the majority of cases will simply ignore them as the attack will not be severe enough to warrant any action.
DDoS attacks manifest in a number ways and are often achieved as a result of malware or trojans being used to send requests to a target IP. Computers infected with these programs are coordinated to simultaneously flood a target IP (or IPs) with requests.
The distributed nature of the problem is one of the main reasons why DDoS attacks can be so difficult to deal with. This simple diagram reveals how a single computer can manage a network of handlers and from there, many thousands of compromised PCs, to be able to control an attack:
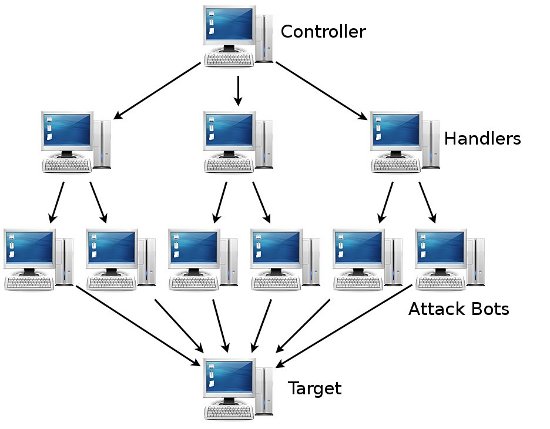
Many attacks fail in the process as the resources mentioned above, bandwidth and web-sessions, are, by design, in ample supply or are themselves widely distributed. However, DDoS attacks are becoming more common and increasingly successful.
A significantly powerful attack can also cause an ISP network as a whole to degrade due to excessive bandwidth demands. So how does an ISP mitigate these extreme situations?
For ISPs, with potentially 1000s of other customers to consider, sometimes it is simply better to sacrifice the target IP for the greater good, make it disappear from the network, and thereby avoid the associated malicious traffic directed towards it. This sacrifice of a target IP is known as blackholing or null routing.
Such a powerful attack can also cause an ISP network as a whole to degrade due to excessive bandwidth demands
To achieve successful blackholing, the downstream ISP must have the ability to direct it's upstream ISP to stop forwarding any 'attack' packets destined for the target IP onto its network. The upstream ISP simply drops the packets - blackholes them - before they reach the downstream ISP.
Blackholing effectively completes the DDoS by making the targeted IP unreachable from other ISP up-streams, but removes the effects of the malicious traffic from the network, thus allowing normal service. Blackholing is a simple, effective solution but also a last resort. Although the network as a whole is spared, the target IP is now off-line and the DDoS has triumphed.
Blackholing is a simple effective solution but also a last resort
Yet, other options exist depending on the profile of the attack. If, for example, the source of DDoS service requests is less distributed, firewall filters can be used. In other words, if there are identifiable source IPs which are either creating all or a large part of the offending service requests, then it may be possible to filter these IPs at the network edge or ingress points. Firewall filtering works well in these situations so long as bandwidth resources are not saturated external to the firewall.
All the same, DDoS attacks are tricky to block quickly through firewalling without some kind of automation. ISPs can benefit from the addition of an automation bridge between network flow analysis and firewall filters. Again, however, the size of attack will always be a concern and black-holing may still be necessary.
Perhaps the most effective way to deal with DDoS assaults is to sign up to a professional DDoS mitigation service such as Akamia's DDoS Defender. Interestingly, Akamai's fascinating Real-Time Web Monitor reveals that the UK is a fairly safe area in DDoS vulnerability terms by global comparison:
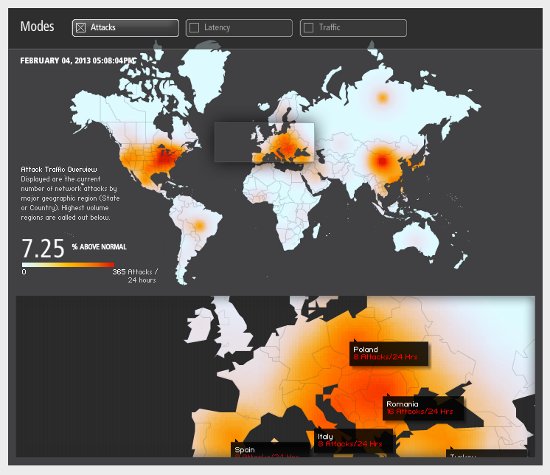
DDoS mitigation services work through intercepting BGP route advertisements from their clients and 'cleansing' or 'scrubbing' inbound traffic. In other words, they act as a huge inbound firewall for customers running BGP networks (for more on BGP networks, see this earlier blog). DDoS mitigation services are notoriously expensive and range from proactive (more expensive) to reactive (less expensive but requires manual intervention and takes longer to mitigate). However, if your site is vulnerable and uptime critical, mitigation services are your best bet.
Come join us on: