Secure connectivity over the Internet
Fri, 3 May 2013
This blog post takes a look at some of the options available for creating secure connections over the internet.
Whilst Internet based connections do not have the benefits of managed private circuits, as discussed in an earlier post, they do offer other advantages including lower costs and portability.
The main difference between private circuits and Internet based connections is that they fundamentally operate at different layers of the OSI model. A private circuit is private because, operating at layer 2, the bit stream connection between devices never enters the Internet at large.
Operating at layer 2, the bit stream of a private circuit connection between devices never enters the internet at large.
A private connection either stays within the networking space of a single ISP, or connects externally, yet still at layer 2, via dedicated physical or virtual interface; in essence, we can say that it is non-routed as it does not rely on the globally covered IPv4 routing table to reach its destination; click here read more about how the different network layers operate.
By contrast, a secure Internet connection is routed over the web. Data transfer goes over this public medium and as such, is vulnerable to any and all interception by nefarious parties of all hues. Technologies available for the protection of data being transferred over the public Internet all rely on one common method: Encryption.
A common use of encryption for secure internet based connections is the SSH protocol. SSH is most often used by sys-admins and programmers to gain access to their servers and applications from remote locations. Accessing over the Internet means they can be anywhere is the world and yet still gain secure access to their operating systems and web services.
Whilst many Linux distributions allow users to run the client SSH program from the command line, Windows based access is most often initiated by a GUI access tool, such as the venerable PuTTY.
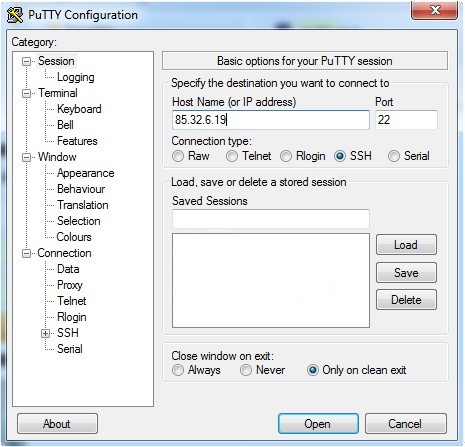
PuTTy can access various server connection types including SSH
As with many encryptions techniques, SSH uses the well known public-private key cryptography technique for authentication. The concept is, in fact, quite simple: If I connect to a host server from a command line or from the PuTTY client using just the IP or domain name, the host will send me a public key. This key is not a secret but is used to perform an encryption on the subsequent data I send back to the server, in this case, my user name and password to authenticate and gain access.
The host who gives away the public key also maintains a secure private key - which provides the only way to decrypt the data sent.
The public key’s only job is to encrypt my authentication data in a way that is all but interpretable. However, the host who gave away the public key also maintains a secure private key which provides the only way to decrypt the data I have sent. Simply put, the host’s private key is needed to decrypt what its public key has encrypted – without it, the data is scrambled and useless.
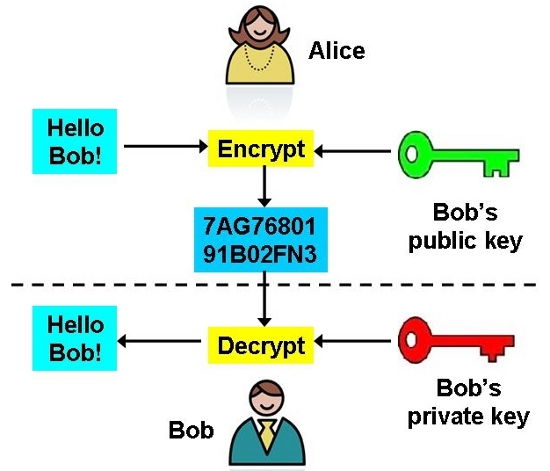
Before Alice sends any sensitive data, she encrypts it with Bob’s public key
A similar process is used to select the cipher so that data can be sent. The cipher is a technique of encrypting and decrypting data on the fly, so that a session can be created and data exchanged. SSH is a powerful and reliable connection tool that can also be used to bypass firewalls with a technique know as port forwarding. However, set up can be cumbersome to manage for non-technical staff as it is generally used a the command line.
SSH set up can be cumbersome to manage for non-technical staff as it is generally used a the command line.
For a more use friendly ‘over the Internet’ connection, administrators, including ConnetU engineers, will often configure a VPN. This is a way of using the internet as the medium to create a secure tunnel either between two LANs or between a remote client, a laptop or a home PC, and a day-to-day office LAN. Once a VPN is set and running, file systems and some software services can be accessed and run through a remote LAN, or client, as if it were physically connected to the other.
Once again, encryption plays its role. In a connection between two LANs over the public internet, a VPN device (firewall) can be used to maintain encrypted communication at high speeds. In a typical Juniper IPsec site-to-site (LAN-to-LAN) VPN, ConnetU engineers have seen transfers of up to 40Mbps.
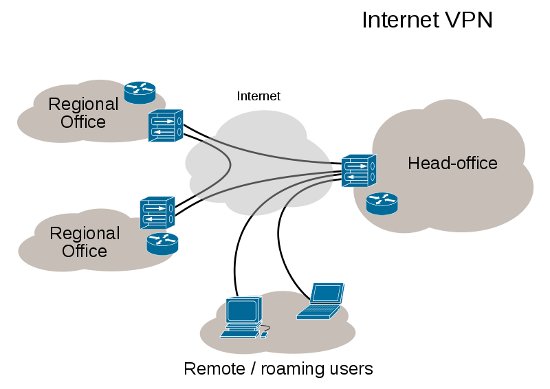
A VPN can provide over the internet connections between office LANs as well as from individual remote clients to central office LANs
IPsec is the common encryption method for site-to-site VPNs and has the option of using powerful encryption algorithms such as 3DES and AES. With encryption rates of up to 256 bits, there is very little chance of uncovering the key and deciphering the transmission. Furthermore, the functionality is usually included in most firewalls and licensed for dozens/hundreds of endpoints, meaning many users in one office can access the LAN of the other office or data centre.
As mentioned above, a VPN can also consist of a Juniper, or other vendor device, and a VPN client, or number of clients, installed on home PCs or roaming laptops and smart phones. This service allows remote users to securely log on to their office LAN from anywhere in the world with a decent Internet connection. The process involves either client software on the remote device that coordinates authentication and encryption, or the use of SSL certificates.
SSL uses a similar public key method as SSH, but is automated through a web browser that agrees the cipher and handles the session. SSL connections are configured to allow access only specific users.
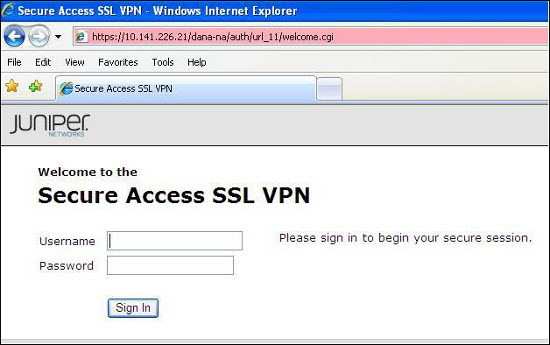
A typical SSL login page as seen by the remote client, using the secure **https** protocol
As the Internet gets faster and more reliable, Internet based connectivity, as opposed to leased lines and private circuits, is maintaining its activeness as a core inter-site secure networking option.
Furthermore, the use of client VPN software and SSL certificates for browser VPN connections on selected user devices (including BYOD) is also gaining in popularity as companies and organisations continue to empower their workforce with Internet ready devices.
Come join us on: